
Call the exorcist
administrator, folks! The Head Accountant caught a powerful virus; all is lost!
It is a common situation based on the human factor, latest virus trends and motivated
hackers. Indeed, why should the violators poke around someone else’s software,
if they can rely on the company’s employees?
The major corporations’ products are constantly getting cracked, although their security issues are a job scope of hundreds of experienced people.
Meantime, regular person is way more vulnerable to the hacker attacks. But keeping our heads straight, no maleficent wants a one lonely account, the goal is to get a large base of potential victims and treat it with “chain letters”, spam or viruses. And speaking of our personal data security – we ourselves handing out all the private information right and left.
Hot Virus Trends
The distinguishing feature of all recent viruses and hacking techniques is that they interact with the person, not the system. That is, the victim starts the breaching process. It’s the “social engineering” – a method of illegal access to information based on the features of human psychology. And if in the past the attackers had to turn into a real detective, track down their goals, communicate, sometimes even get a job to hack the company from the inside – now we can say a big thanks to social media. They simplified and accelerated the process of gathering information greatly.
Going through the Twitter, Facebook and Instagram of the target, you’ll get an accurate person’s profile with a phone number, email, names of parents, friends and other details. It's all free of charge – enjoy!

And if the fraudsters will get access to the corporate e-mail of one of your employees, spam mailings threat not only everyone within the company, but also your customers. In another case, the attackers disable the employee’s computer for a long time, by sending some “report” on mail.
Hackers plan attacks on those who work with valuable information – the secretaries, managers, accountants, HRs.
Since the recovery of documents, system, website, or receiving a password will cost you a bundle, it’s necessary to understand what we are dealing with. In order to defend from all of these “social engineers” effectively, we want to pull down one of the latest virus designs.
“Cryptoviruses”
Encrypting malware spreads via email, disguised as serious documents: summons, invoices and requests from the tax agency. It's essential to be all eyes, so you won’t install the malware by accident. Our technical experts specifically analyzed one encrypting virus, so we would be able to show to what you need to pay attention:
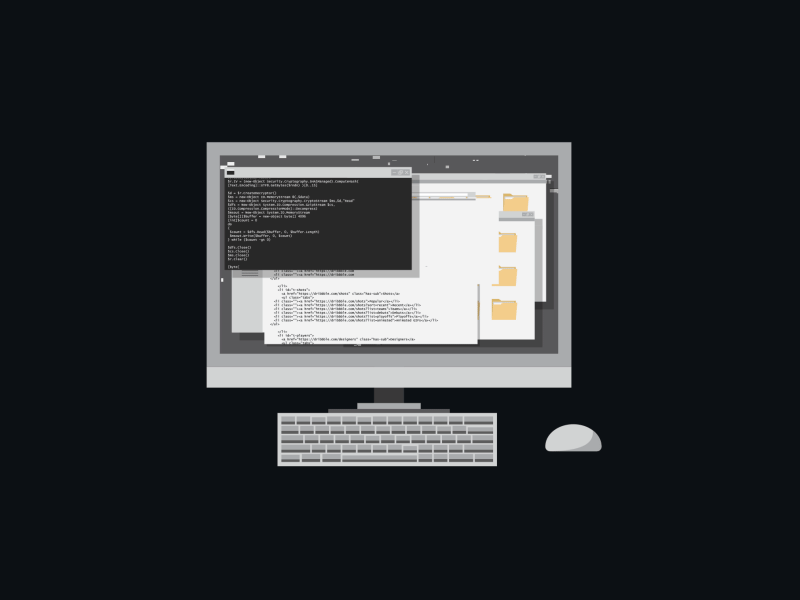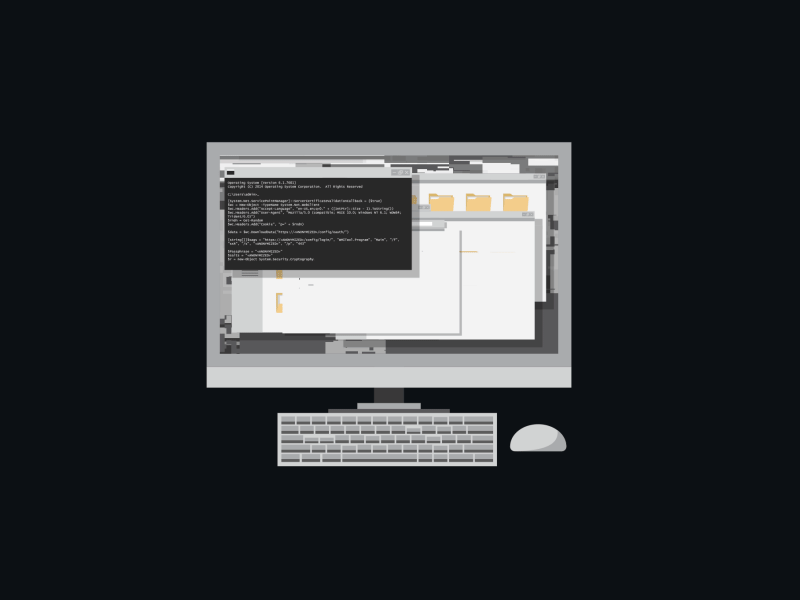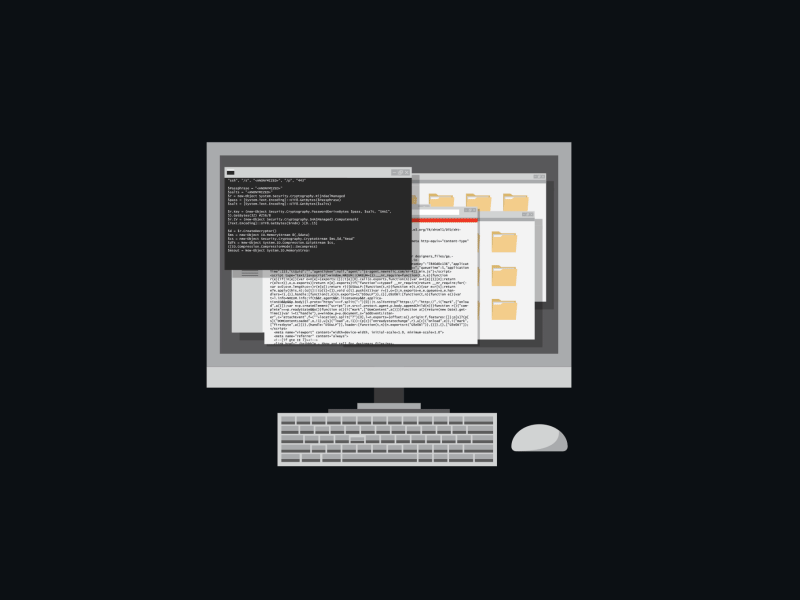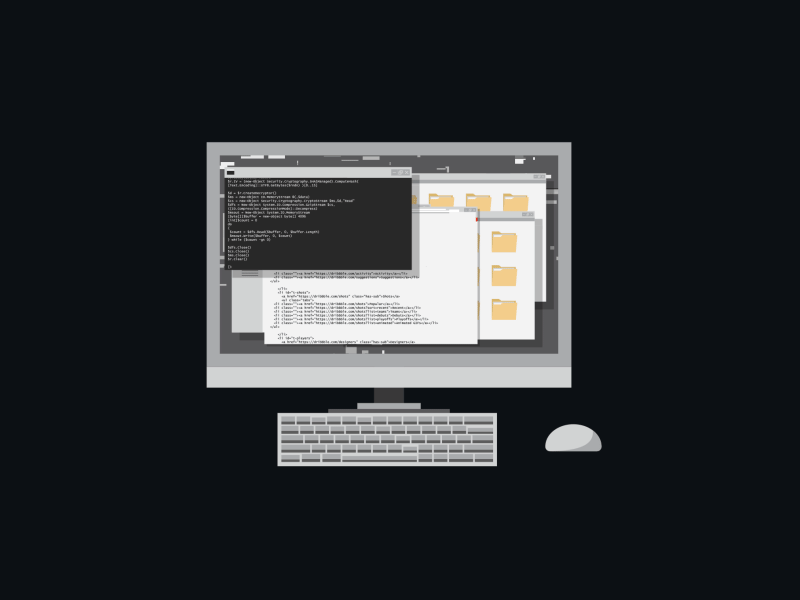
Watch, how it's done:
Attention! If a cryptographer has infected your computer, then with a probability of 95%, your information will be lost irretrievably. After downloading and running the malicious file, it accesses the remote server and downloads the virus code. Then all data on the computer gets encrypted with a random sequence of characters.
To “decode” the files, you will need a key that only the hacker has. The scammer promises to decrypt the information back at a certain amount, but not the fact that it would happen. Sure, it's much easier to leave the person both without the money and data: contracts, acts, instructions, any valuable and sensitive information. So backup important documents, and you'll sleep so much better. In this situation, it's your only 100% protection against viruses.
Pay attention to the above-described features, and you can prevent hazardous incidents when your computer is locked and important information is deleted. In any case, the elimination of the critical vulnerabilities’ consequences will come out much more expensive than just being cautious.
So here's 6 tips for virus detection and prevention of infection:
1. Keep your operating system and programs up to date. Important updates, which are installed automatically by default, can be disabled. But we don't recommend to do it, because the new versions often close the freshly found security holes in software.
2. Install an antivirus and regularly update its database. 100 000 new malicious files are detected daily!
3. Turn on the file name extensions show by: Control Panel \ Folder Options \ View \ Advanced Settings, deselect the “Hide extensions for known file types” and click OK. This way you will always see the real file name extension. Most often, the disguised viruses look like this: file_name.doc.js and file_name.pdf.exe. The actual file extension is .js and .exe, and all that in front of them is a part of the file’s name.
4. Back up your important files – working papers and photos. The frequency of backups should be chosen depending on the frequency of file changes. You can use a cloud service, if it provides an option of returning to old versions of files and adjusting the manual sync. Then, when if the computer is infected, the virus will not get into the cloud. We also recommend that you keep a copy of important data in the archive. Most viruses can’t enter the archive, and all archived information is easily restored after your PC is cleaned up.
5. Increase the professional competence of your employees! As we have said, hackers fit their attacks to our psychology, and constantly improve their techniques. Don’t think that anybody but your company and team would click/download/enter personal data. Anyone can be snared; the task is only in striking the right note. So teach your employees – individually, in team, while playing or in any other possible way!
6. Watch out for emails, texts in your teams’ messengers and any other incoming information. Check the addresses of senders, attachments and email’s content. In order to harm your computer, most viruses require the manual start.
We hope that you read this article as a precaution, not because everything is already bad. We wish you’ll never have a total uncontrolled spam situation or loss of documentation for six months. Follow the above-described six steps, keep your eyes open, and we wish your information remain confidential!
Previous article
Pricing Models. Time & Material
Next article
Inside back of outsourcing: pros and cons